Built-In Security for every Stage
Replit includes pre-deployment scanning and secure-by-default settings to help you build safer apps from the start. For teams building apps at work, we also offer advanced features like SSO, SOC 2 compliance, Private Deployments, and Role-Based Access Controls - giving you the security and control you need at scale.







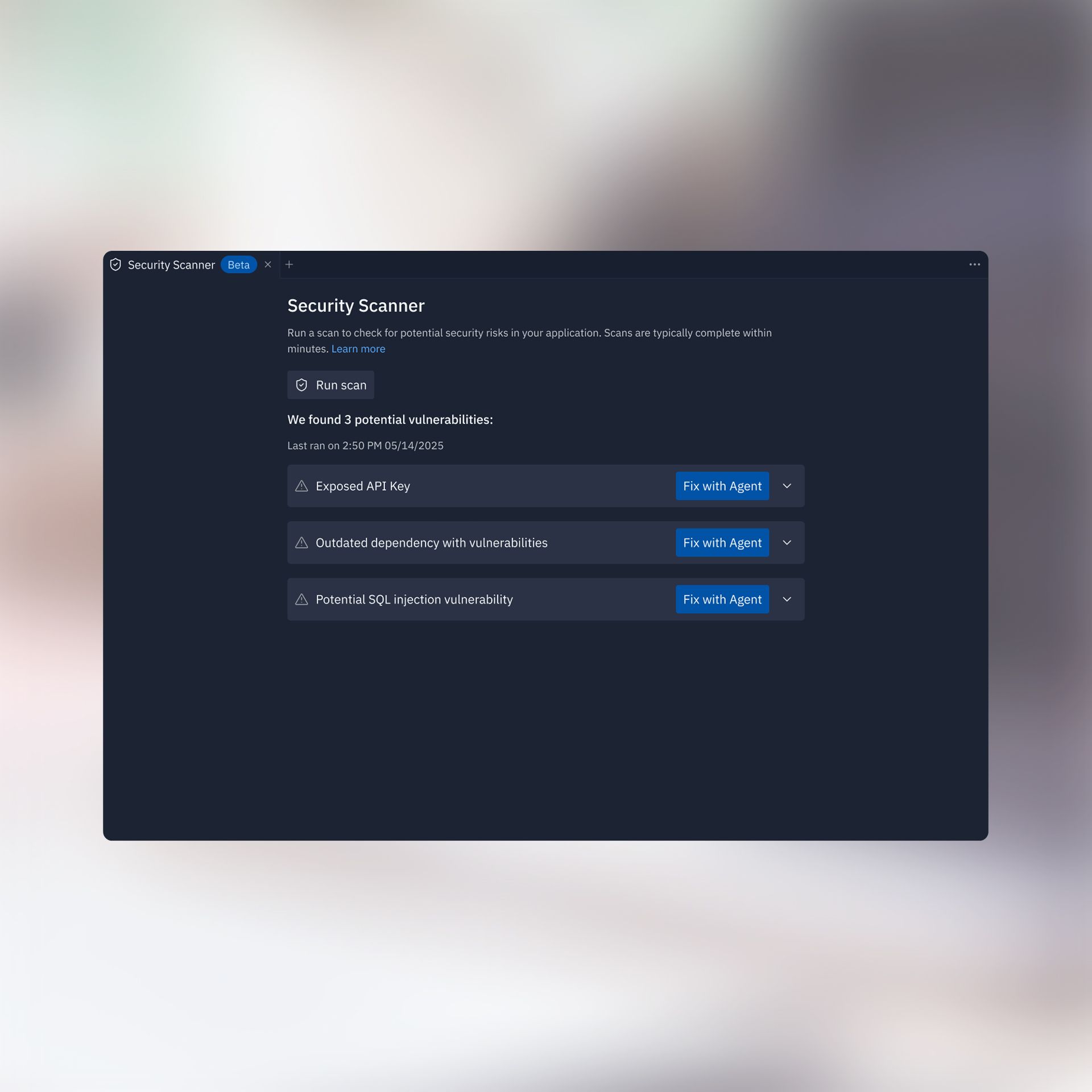
Pre-Deployment Security Scanning
Catch and fix vulnerabilities before you ship. Replit now offers optional pre-deployment security scans powered by Semgrep.
Run a scan before deploying your app to automatically detect potential issues in your code.
See something that needs fixing? Just click “Fix with Agent” and let Replit Agent handle the rest.
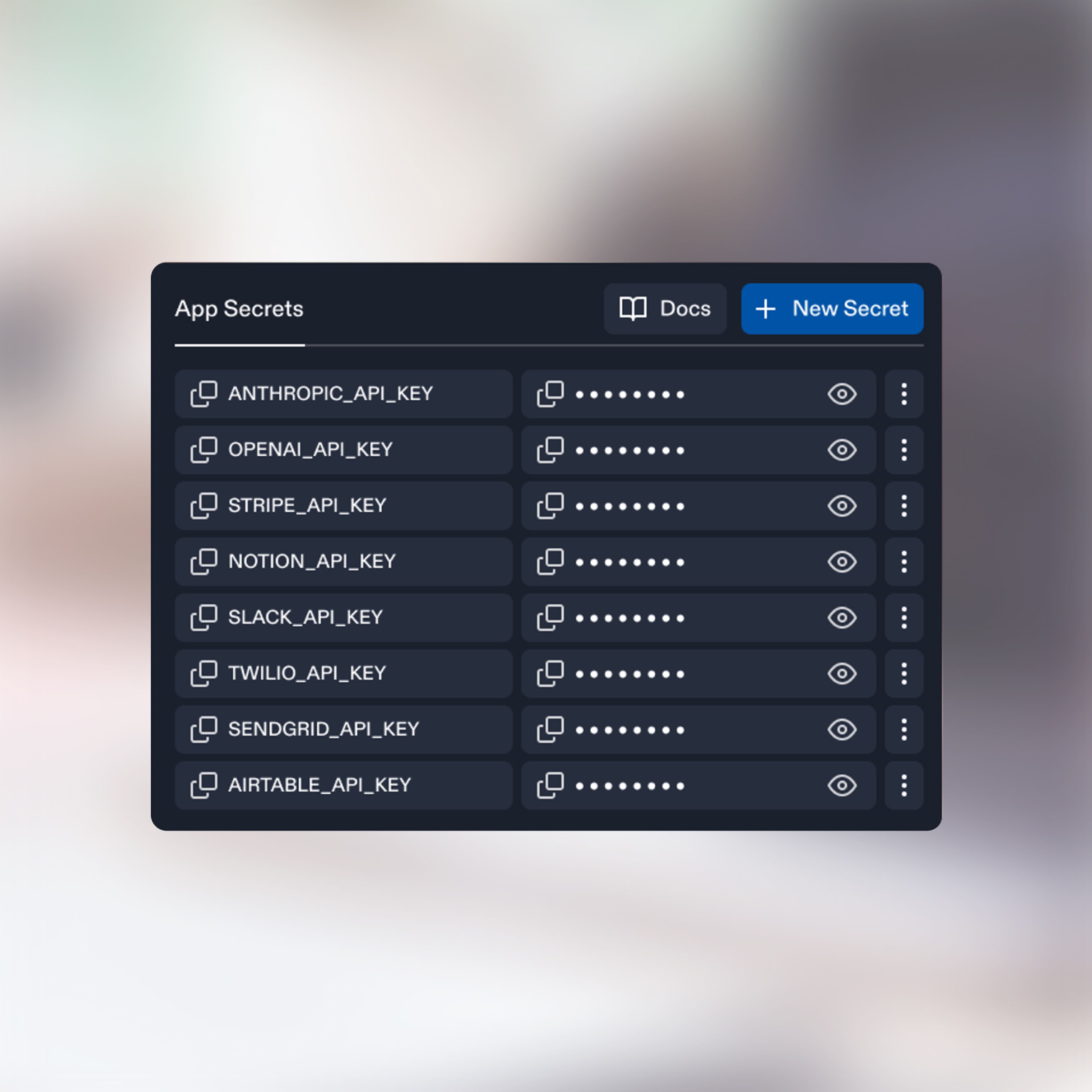
Better Defaults for keeping API Keys secure
Replit automatically checks your prompts to prevent sensitive information like API keys from being exposed.
If you try to include an API key in a prompt, we’ll guide you to use our secure Secrets tool instead and make sure your secrets stay secret.
Secrets are encrypted using Google Cloud’s secure storage and are safely accessible from your application’s code.

Cloud Based Sandbox Environment for Deployment Security
All Replit deployments are securely backed by Google Cloud Platform (GCP)
App Deployments run on GCP
Object storage uses Google Cloud Storage (GCS)
Resource isolation between projects
DDoS protection through Google Cloud Armor
The safest place for vibe coding
Vibe coding makes software creation accessible to everyone, entirely through natural language. Whether it’s personal software for yourself and family, a new business coming to life, or internal tools at your workplace, Replit is the best place for anybody to build.

SSO for secure access
Seamlessly onboard entire departments securely through your existing identity provider.

SOC 2 for enterprise
Create with confidence. Replit is SOC 2 compliant and meets rigorous security standards, empowering your orgs to develop mission-critical applications.

Private deployments to protect innovations
Share and test internal prototypes securely. Ensure only authorized team members can access your projects before they're ready for the world.

Role-based access control
Easily map your identity framework and assign specific roles to individuals or groups. Manage invites with SCIM. Control who can view, edit, or deploy your applications.
